How to bypass Android certificate pinning and intercept SSL traffic
by vavkamil
7 minutes to read
Over the last few months, I had a quite luck finding IDOR vulnerabilities in mobile API of Android applications. Nowadays most of the apps are obfuscated and using certificate pinning to prevent MiTMs.
If you are late in the game or want to shift your bug bounty hunting on Android apps, there are awesome tools that can help you catch up fairly quickly :)
I'm myself using an older rooted phone with Burp Suite and tools mentioned bellow.
Prerequisites:
- smartphone with rooted Android 7+ (I'm using Nexus 5x with latest LineageOS; Android 8.1.0)
- computer with Linux (latest Ubuntu is just fine)
Requirements:
- Burp Suite (community edition is fine)
- ADB (sudo apt-get install adb OR sudo yum install android-tools)
- Frida (pip install frida-tools)
- Objection (pip3 install objection)
Intercepting HTTPS traffic
Since the Android Nougat 7.0 (API >= 24), it is no longer possible to simply install the Burp Suite CA certificate, as it's no longer trust user or admin-added CAs for secure connections, by default.
Protection of all application data is a key goal of the Android application sandbox. Android Nougat changes how applications interact with user- and admin-supplied CAs. By default, apps that target API level 24 will—by design—not honor such CAs unless the app explicitly opts in. This safe-by-default setting reduces application attack surface and encourages consistent handling of network and file-based application data.
https://android-developers.googleblog.com/2016/07/changes-to-trusted-certificate.html
For the guide on how to install Burp cert as a system with root permissions, best description that I come over was from @ropnop, so please look at his article Configuring Burp Suite with Android Nougat.
Thanks to the @securitychops, we have one liner that will do everything for you :)
Next, you need to install Frida framework to your PC. The best way to install Frida’s CLI tools is via PyPI:
$ pip3 install frida-toolsFrida is like Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps. Frida also provides you with some simple tools built on top of the Frida API. These can be used as-is, tweaked to your needs, or serve as examples of how to use the API.
It also needs to run on the phone, so enable USB debugging and connect to your device. To install ADB & Fastboot on Ubuntu systems, execute the following command from the terminal:
$ sudo apt-get install android-tools-adb android-tools-fastbootI prefer connection over the network because sometimes I don't have USB-C cable laying around and this is a workaround most of the time.
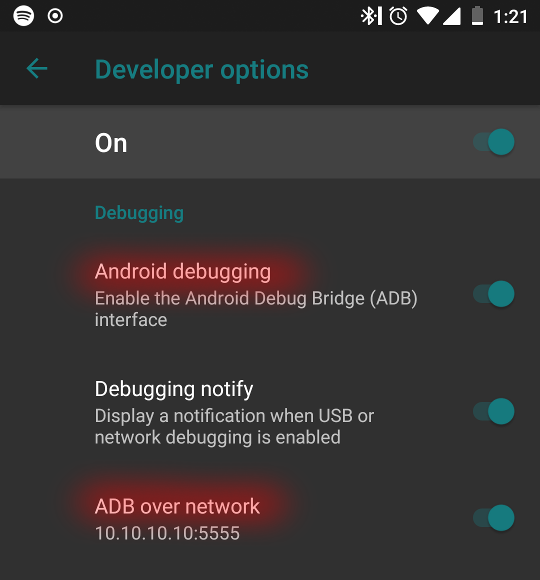
On the phone, allow debugging in Settings/System/Developer options and turn on `ADB over network`. You should be able to connect like this:
$ adb connect 10.10.10.10:5555
* daemon not running; starting now at tcp:5037
* daemon started successfully
connected to 10.10.10.10:5555
$ adb root
restarting adbd as root
$ adb connect 10.10.10.10:5555
connected to 10.10.10.10:5555
$ adb shellNow you need to download frida-tools to your device and start the service. There is a nice guide from @dpnishant how to do that:
$ wget https://github.com/frida/frida/releases/download/12.7.0/frida-server-12.7.0-android-arm64.xz
$ unxz frida-server-12.7.0-android-arm64.xz
$ mv frida-server-12.7.0-android-arm64 frida-server
$ adb push frida-server /data/local/tmp/
$ adb shell "chmod 755 /data/local/tmp/frida-server
$ adb shell "/data/local/tmp/frida-server &
Don't forget that root permissions on the phone are required. Next, start the installation of Objection using pip3 with:
$ pip3 install objectionObjection is a runtime exploration toolkit powered by Frida. There is an awesome article from the author himself. It has a lot of cool features for both Android and iOS.
At this point, frida-server is running on the phone, you are connected over adb from the PC and have installed all prerequisites.
To be able to use a smartphone with Burp Suite, you need to change proxy listener from Loopback only to All interfaces.
And modify Wi-Fi on the phone. In the advanced options you can change proxy settings, so with the manual settings enter the local IP and port for Burp Suite.
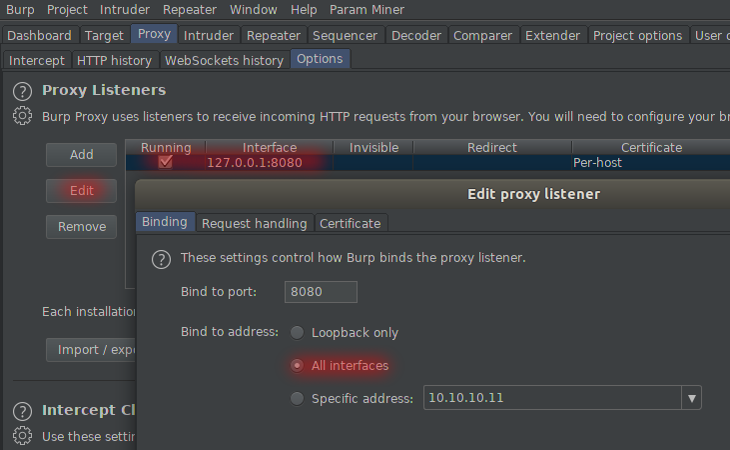
Burp - All interfaces 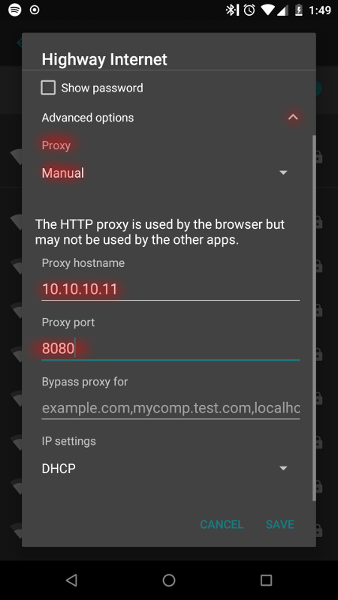
AndroidWi-Fi proxy - Burp IP
Finally, its time to select any installed Android application and try to bypass certificate pinning and see requests in Burp suite. With Frida, you list application on the phone like this:
$ frida-ps -UaOr if you already know the identifier of the application, for example com.*******.kln, hook it with Objection like this:
$ objection -g c**********n explore -qAnd the best part is that after running:
# android sslpinning disableyou should be able to see all requests from a mobile application in Burp Suite with successfully bypassed certificate pinning.
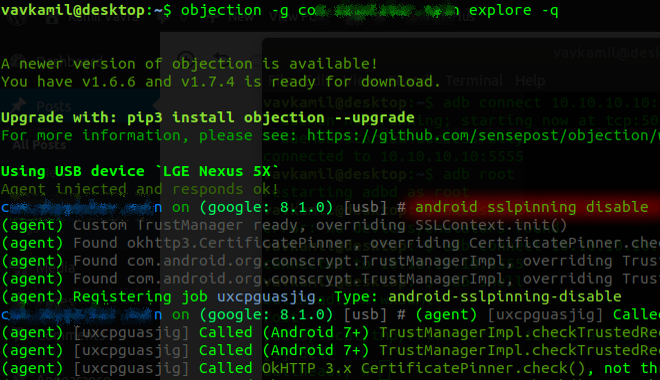
Sometimes if you experience some issues, for example with Facebooks authentication or things like that, it's best to configure "SSL Pass Through" in "Burp Suite > Proxy > Options" check Automatically add entries on client SSL negotiation failure.
Back to the Burp proxy, I once did this entire setup and the first thing that I saw in HTTP history was this request:
GET /api/2.0/user/64296783669/messages HTTP/1.1
X-SessionId: d98d861ef5fd
X-Token: ak1tUXhPRFl5WkdZeU1qa3pOakZrT0RJMFpUazVaV1E1Wmc=
User-Agent: App|Android|2.0.0.0|2.3
Connection: close
Host: redacted
Accept-Encoding: gzip, deflateand just by modifying userID was able to see other user's messages :) That was a lucky day.
Resources:
https://www.frida.re/
https://www.frida.re/docs/installation/
https://support.google.com/nexus/answer/2844832?hl=en
https://sensepost.com/blog/2017/objection-mobile-runtime-exploration/
https://omespino.com/tutorial-universal-android-ssl-pinning-in-10-minutes-with-frida/
https://github.com/sensepost/objection/wiki/Installation
https://github.com/sensepost/objection
https://github.com/frida/frida/issues/597
https://github.com/dpnishant/appmon/wiki/5.a-Setup-on-Android-%5BRooted%5D
https://gist.github.com/davidnunez/1404789
https://blog.ropnop.com/configuring-burp-suite-with-android-nougat/
https://blog.netspi.com/four-ways-bypass-android-ssl-verification-certificate-pinning/
https://blog.jamie.holdings/2018/09/05/bypass-certificate-pinning-on-android/
https://www.notsosecure.com/pentesting-android-apps-using-frida/